cyber-hygiene
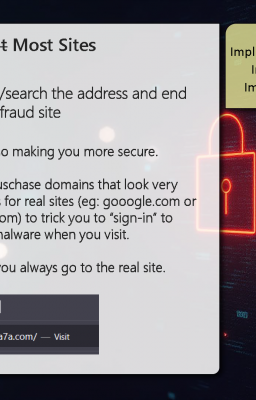
Cyber Security Hygiene (Proactive) Bookmark Most Sites
Cyber-criminals frequently purchase domains that look very similar or are common typos for real sites to trick you. Using a bookmark ensures you always go to the real site.